Threat Watch
Threat Watch delivers instant insights to assess and enhance your cybersecurity health across critical security categ...
Visit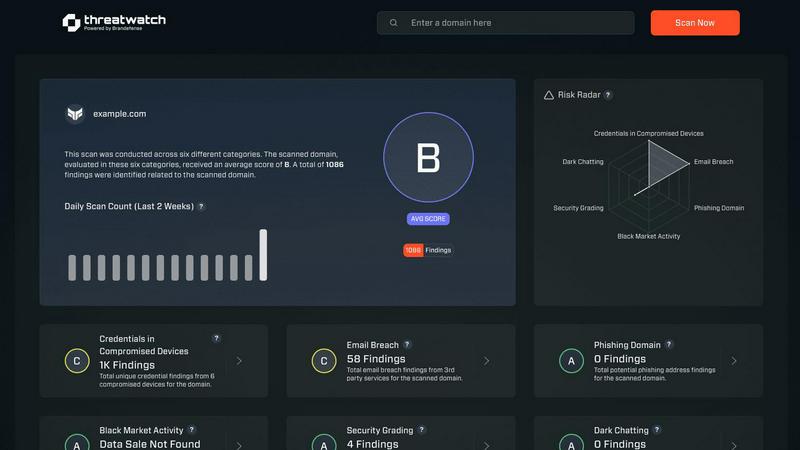
About Threat Watch
Threat Watch is a cutting-edge cybersecurity intelligence solution designed to empower organizations by providing a comprehensive overview of their cyber health. This tool meticulously analyzes an organization's digital assets, vulnerabilities, and exposures, enabling users to swiftly identify and address potential risks. By leveraging real-time insights and automated assessments, Threat Watch offers a clear picture of security threats, allowing businesses to prioritize and mitigate risks effectively. It is particularly beneficial for IT professionals, cybersecurity teams, and organizational leaders who seek to bolster their defenses against ever-evolving cyber threats. With its robust capabilities, Threat Watch not only uncovers critical security issues but also enhances the overall cybersecurity posture of any organization, making it an indispensable asset in today’s digital landscape.
Features of Threat Watch
Real-Time Risk Assessment
Threat Watch delivers instant evaluations of your organization's cybersecurity posture, providing real-time insights into potential vulnerabilities and threats. This feature ensures that users can address risks as they arise, minimizing the window of exposure.
Automated Vulnerability Scanning
With automated scanning capabilities, Threat Watch continuously monitors for vulnerabilities across your digital assets. This feature allows organizations to maintain an up-to-date understanding of their security landscape, facilitating faster responses to newly discovered threats.
Dark Web Monitoring
This feature actively scans the dark web for compromised credentials and sensitive organizational data. By identifying potential breaches before they can be exploited, Threat Watch empowers organizations to take preventive measures and safeguard their information.
Comprehensive Reporting
Threat Watch generates detailed reports that summarize findings and provide actionable insights. These reports help stakeholders understand their security status clearly and allow for informed decision-making regarding risk management strategies.
Use Cases of Threat Watch
Early Detection of Breaches
Organizations can utilize Threat Watch to detect breaches early on, enabling swift action to mitigate damage. By continuously monitoring for signs of compromise, businesses can respond to incidents before they escalate.
Prioritization of Security Efforts
With Threat Watch, organizations can prioritize their cybersecurity efforts based on real-time data and risk assessments. This allows security teams to focus their resources on the most critical vulnerabilities, enhancing overall protection.
Compliance and Regulatory Adherence
Threat Watch assists organizations in maintaining compliance with industry regulations by identifying gaps in security posture. By ensuring that security measures are up to standard, businesses can avoid potential penalties and enhance their credibility.
Incident Response Planning
The insights provided by Threat Watch can inform incident response plans, helping organizations prepare for potential security breaches. By understanding their vulnerabilities and threat landscape, businesses can develop more effective response strategies.
Frequently Asked Questions
What types of organizations can benefit from Threat Watch?
Threat Watch is designed for any organization that prioritizes cybersecurity, including enterprises, small businesses, and government agencies. It is particularly useful for IT and security teams.
How does Threat Watch monitor the dark web?
Threat Watch employs advanced algorithms to scan the dark web for compromised credentials and sensitive information related to your organization. This monitoring helps to identify potential threats before they can be exploited.
Is Threat Watch easy to integrate with existing security tools?
Yes, Threat Watch is built to integrate seamlessly with a wide range of existing security tools and platforms, enhancing your current cybersecurity infrastructure without requiring extensive modifications.
How often are the scans performed?
Threat Watch offers continuous scanning capabilities, ensuring that your organization is monitored in real-time for vulnerabilities and threats. Users can also schedule additional scans as needed for specific assessments.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
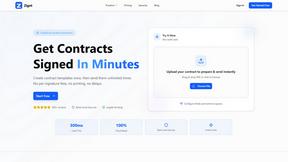
Zignt
Zignt is a secure, AI-powered platform that automates legally binding contract signing and management for businesses.
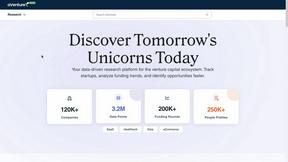
aVenture
aVenture is an AI-driven platform for in-depth research on private companies, investors, and market trends.